Off-page SEO: Strategies for building backlinks and improving domain authority
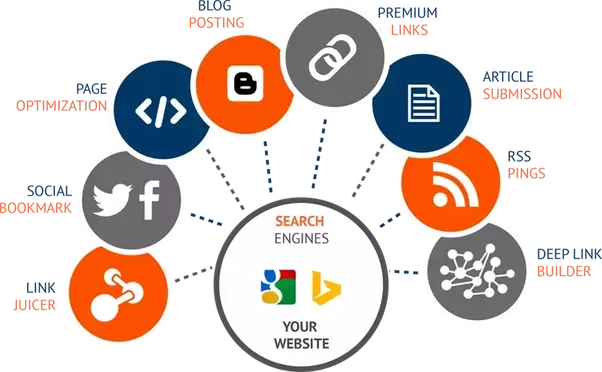
All the actions we do away from your website to raise its search engine rankings are referred to as off-page SEO. This includes techniques for increasing backlinks and the domain authority of the website. Here are some efficient off-page SEO tactics. CONCLUSION Finally, off-page SEO is a crucial component of the entire SEO plan. The […]
THE BENEFITS OF ADOPTING AN AGILE METHODOLOGY FOR SOFTWARE DEVELOPMENT
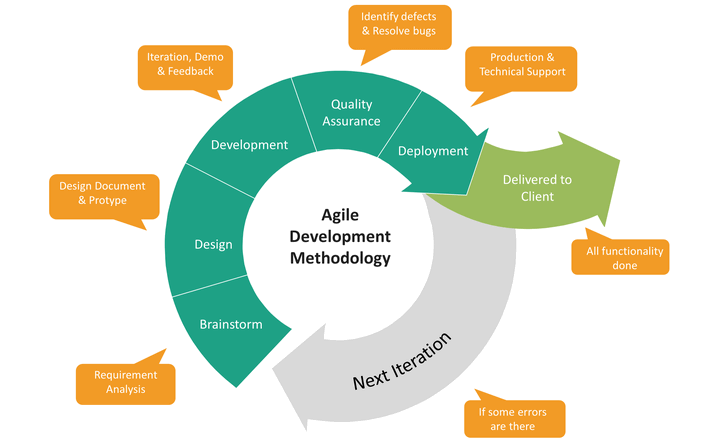
Adopting an Agile methodology for software development can provide numerous benefits for both the development team and the organization as a whole. Here are some of the key benefits: CONCLUSION Adopting Agile technique for software development offers a more adaptable, efficient, and collaborative means of creating software that produces higher-quality solutions more quickly, increasing customer […]
Node Js. : Security Best Practices

Node.js is a well-liked runtime environment for creating server-side applications, however it has security flaws too. To make sure that your Node.js application is secure, just like with any other technology, it’s crucial to adhere to best practises. Several security best practises for Node.js apps will be covered in this blog article. Conclusion Any web […]
MERN STACK: WHY SHOULD WE CHOOSE MERN STACK??
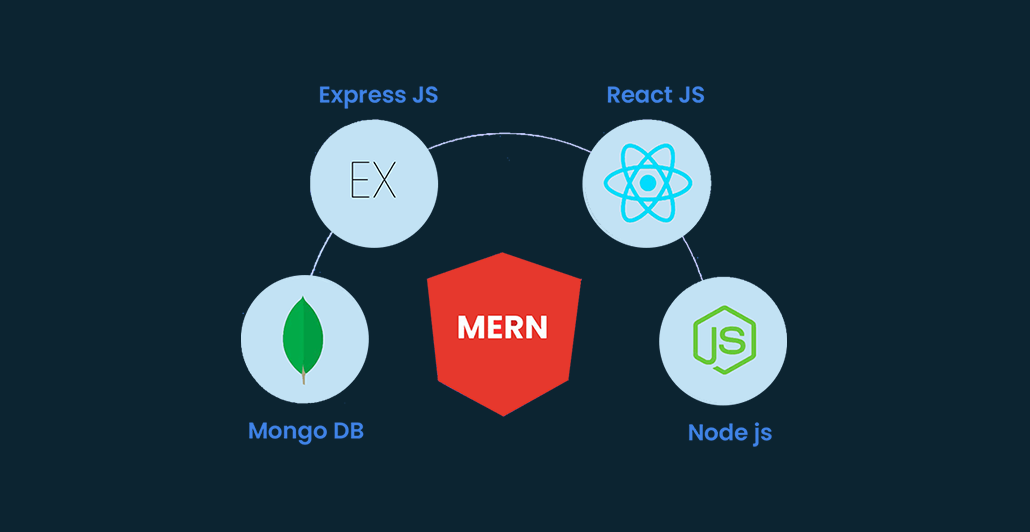
The MERN Stack is a group of strong technologies that are used to create scalable master web applications that include backend, frontend, and database components. Full-stack web apps can be created more quickly and simply using JavaScript. MERN Stack is a user-friendly full-stack JavaScript framework for creating applications and dynamic webpages. Four main elements, or […]
CHAT-GPT & IT’S FUTURE
WHAT IS CHAT-GPT? A highly developed AI system called ChatGPT is able to generate text responses that resemble human speech. It was trained on a large corpus of conversational text and uses the GPT (Generative Pre-trained Transformer) paradigm of operation. As a result, it can answer questions and deliver information in a way that is […]
CLOUD MIGRATION: BENEFITS & LIMITATIONS
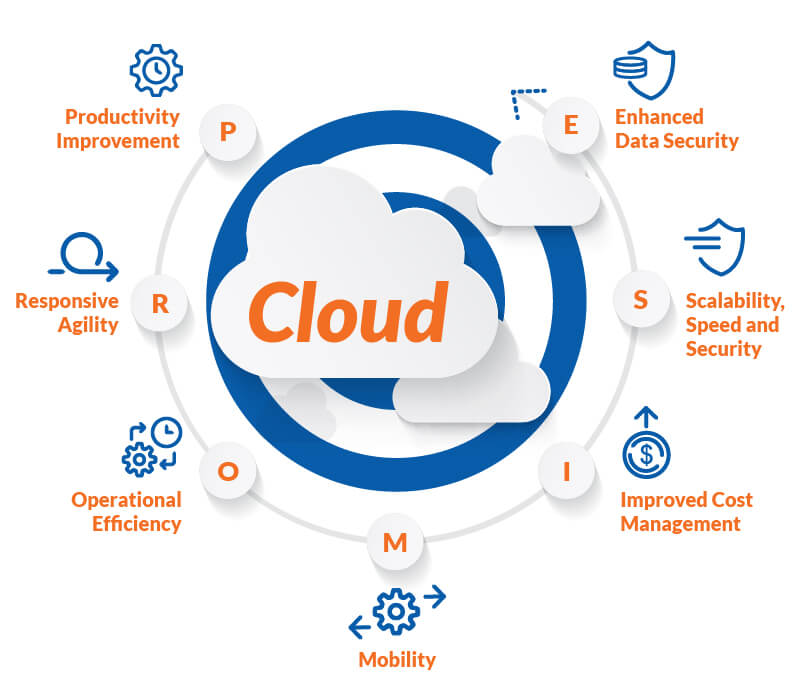
Moving data, applications, or other business components from an on-premises or conventional computing environment to the cloud is referred to as cloud migration. The benefits and challenges of cloud migration will be addressed in this blog. Benefits of cloud migration A major advantage of moving to the cloud is improved flexibility. Businesses can scale their […]
STRATEGIES TO IMPROVE WEB APP SEO

An effective search engine optimization (SEO) strategy can attract people interested in your service and turn them into loyal customers. Web app SEO enables you to produce data-based content to easily attract users to the platform. In concept, SEO works by improving the content of the website, conducting keyword research, and acquiring inbound links to raise […]
BUSINESS PROCESS AUTOMATION: BENEFITS & APPLICATIONS
In order to increase productivity, reduce expenses, and maintain smooth operations, business process automation (BPA) automates routine IT activities and business functions. The global BPA market is anticipated to grow at a CAGR of 12.2% to reach USD 19.6 billion by 2026. Business process automation (BPA) has been widely adopted as a result of a […]
Business Intelligence: What Is It? & What makes it unique from Data science?

BI is a broad phrase that includes descriptive analytics, process analysis, performance benchmarking, and data mining. In this blog, we will explore the meaning of Business Intelligence and what makes it unique from Data Science What is Business Intelligence? Business Intelligence is an umbrella term that comprises the applications, infrastructure, tools, and best practices that […]
Protecting Yourself Online: The Future of Cybersecurity
As technology continues to become more advanced and integrated into everyday life, the need to protect yourself and your information online has become more important than ever. As our digital lives become increasingly intertwined with our real-world lives, it is essential to understand the current state of cybersecurity and the potential threats that exist in […]
